- Ssh Generate Public Key Linux Download
- Generate Public Key Ssh Linux
- Ssh Generate Public Key Linux Windows 10
- Ssh Generate Public Key Linux Server
- Linux Generate Public Private Ssh Key
If you don't already have an SSH key, you must generate a new SSH key.If you're unsure whether you already have an SSH key, check for existing keys. If you don't want to reenter your passphrase every time you use your SSH key, you can add your key to the SSH agent, which manages your SSH keys and remembers your passphrase.
-->
With a secure shell (SSH) key pair, you can create virtual machines (VMs) in Azure that use SSH keys for authentication, eliminating the need for passwords to sign in. This article shows you how to quickly generate and use an SSH public-private key file pair for Linux VMs. You can complete these steps with the Azure Cloud Shell, a macOS or Linux host, the Windows Subsystem for Linux, and other tools that support OpenSSH.
- Mar 31, 2018 Generate public key and store into a file. It is a simple one liner command to generate a public key from a private key, so lets say our private key is named ‘user@myserver.key’ and we want to generate the public key and name it ‘authorizedkeys’. Below is the command to do this.
- Creating an SSH key on Linux & macOS 1. Check for existing SSH keys. You should check for existing SSH keys on your local computer. You can use an existing SSH key with Bitbucket Server if you want, in which case you can go straight to either SSH user keys for personal use or SSH access keys for system use. Open a terminal and run the following.
Note
VMs created using SSH keys are by default configured with passwords disabled, which greatly increases the difficulty of brute-force guessing attacks.
For more background and examples, see Detailed steps to create SSH key pairs.
For additional ways to generate and use SSH keys on a Windows computer, see How to use SSH keys with Windows on Azure.

Supported SSH key formats
Azure currently supports SSH protocol 2 (SSH-2) RSA public-private key pairs with a minimum length of 2048 bits. Other key formats such as ED25519 and ECDSA are not supported.
Create an SSH key pair
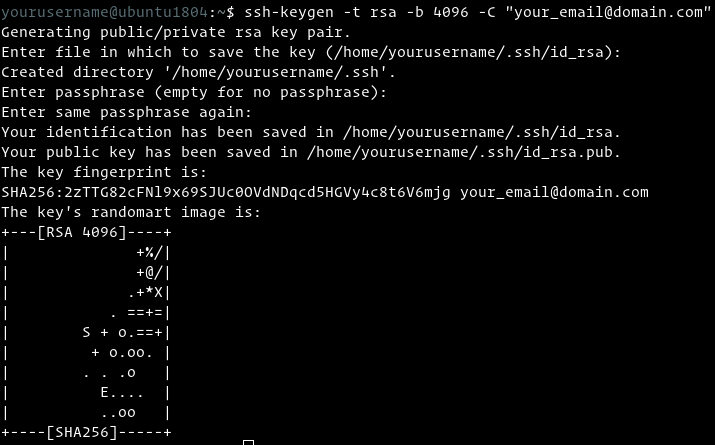
Use the ssh-keygen command to generate SSH public and private key files. By default, these files are created in the ~/.ssh directory. You can specify a different location, and an optional password (passphrase) to access the private key file. If an SSH key pair with the same name exists in the given location, those files are overwritten.
The following command creates an SSH key pair using RSA encryption and a bit length of 4096:
Free gta 5 steam key. If you use the Azure CLI to create your VM with the az vm create command, you can optionally generate SSH public and private key files using the --generate-ssh-keys option. The key files are stored in the ~/.ssh directory unless specified otherwise with the --ssh-dest-key-path option. The --generate-ssh-keys option will not overwrite existing key files, instead returning an error. In the following command, replace VMname and RGname with your own values:
Provide an SSH public key when deploying a VM
To create a Linux VM that uses SSH keys for authentication, specify your SSH public key when creating the VM using the Azure portal, Azure CLI, Azure Resource Manager templates, or other methods:
If you're not familiar with the format of an SSH public key, you can display your public key with the following cat command, replacing ~/.ssh/id_rsa.pub with the path and filename of your own public key file if needed:
A typical public key value looks like this example:
If you copy and paste the contents of the public key file to use in the Azure portal or a Resource Manager template, make sure you don't copy any trailing whitespace. To copy a public key in macOS, you can pipe the public key file to pbcopy. Similarly in Linux, you can pipe the public key file to programs such as xclip.

The public key that you place on your Linux VM in Azure is by default stored in ~/.ssh/id_rsa.pub, unless you specified a different location when you created the key pair. To use the Azure CLI 2.0 to create your VM with an existing public key, specify the value and optionally the location of this public key using the az vm create command with the --ssh-key-values option. In the following command, replace VMname, RGname, and keyFile with your own values:
If you want to use multiple SSH keys with your VM, you can enter them in a space-separated list, like this --ssh-key-values sshkey-desktop.pub sshkey-laptop.pub.
SSH into your VM
With the public key deployed on your Azure VM, and the private key on your local system, SSH into your VM using the IP address or DNS name of your VM. In the following command, replace azureuser and myvm.westus.cloudapp.azure.com with the administrator user name and the fully qualified domain name (or IP address):
If you specified a passphrase when you created your key pair, enter that passphrase when prompted during the login process. The VM is added to your ~/.ssh/known_hosts file, and you won't be asked to connect again until either the public key on your Azure VM changes or the server name is removed from ~/.ssh/known_hosts.
If the VM is using the just-in-time access policy, you need to request access before you can connect to the VM. For more information about the just-in-time policy, see Manage virtual machine access using the just in time policy.
Next steps
For more information on working with SSH key pairs, see Detailed steps to create and manage SSH key pairs.
If you have difficulties with SSH connections to Azure VMs, see Troubleshoot SSH connections to an Azure Linux VM.
Introduction
SSH (Secure Shell) is a network protocol that enables secure remote connections between two systems. System admins use SSH utilities to manage machines, copy, or move files between systems. Because SSH transmits data over encrypted channels, security is at a high level.
This article will guide you through the most popular SSH commands. The list can also serve as a cheat sheet and will come in handy the next time you need to complete a task.
- An SSH client of your choice
- An SSH server on the remote machine
- The IP address or name of the remote server
To connect to a remote machine, you need its IP address or name. Load the terminal or any SSH client and type ssh followed by the IP address:
or name:
The first time you connect to a host, you’ll see this message:
Type yes and hit enter. You may need to enter your password as well.
SSH uses the current user when accessing a remote server. To specify a user for an SSH connection, run the command in this format:
For instance:
By default, the SSH server listens for a connection on port 22. If the port setting in the SSH config file has been changed, you’ll need to specify the port. Otherwise, you will get this error:
To connect to a remote host with a custom SSH port number, use the -pflag. For example:
To improve the security of SSH connections, generate a key pair with the keygen utility. The pair consists of a public and private key. The public key can be shared, while the private key needs to stay secure.
SSH key pairs are used to authenticate clients to servers automatically. When you create an SSH key pair, there is no longer a need to enter a password to access a server.
On the host machine’s terminal, use this command to create a key pair:
To use default settings, hit Enter on the prompts for file location and passphrase.
To use the key pair for SSH authentication, you’ll need to copy the public key to a server. The key is the file id_rsa.pub previously created with SSH keygen utility.
To copy your key to a server, run this command from the client:
You can also specify a username if you don’t want to use the current user.
Enter the password to authenticate when asked. After this, you will no longer need to use the password to connect to the same server.
You can securely copy files over the SSH protocol using the SCP tool. The basic syntax is:
For example, to copy a file sample3 to your Desktop on a remote server with a username test, type in:
The output shows a summary of the operation.
Make sure to use the uppercase-Pflag if you need to specify the port.
You can control how remote users can access a server via the SSH. Edit the settings in the sshd_config file to customize SSH server options. Make sure to edit only the options you are familiar with. A server can become inaccessible due to bad configuration.
Use the editor of your choice to edit the file. You’ll need superuser permissions to make changes. In Linux, we use vim:
In the command line on a remote host, type in:
Enter the sudo password, and the shell opens the file in the editor you used.
When you make changes to the SSH configuration, you’ll need to restart the service in Linux.
Depending on the Linux distro, run one of the following commands on the machine where you modified the settings:
or:
Finally, enter the password to complete the process. As a result, the next SSH session will use the new settings.
Working on a remote server using SSH requires knowing basic SSH commands. Use the commands and options in this article to manage a remote host. Note that you can combine the flags to get the output you need.
Use the pwd command to show the file system path.
The output displays the location of the directory you are in.
To list the contents of a current working folder, use the ls command.
The shell will show the names of all directories, files, and links. To get more information, add one of the following flags:
-adisplays hidden files and entries starting with a dot.-lshows file details for directory contents. For example, the output includes permissions, ownership, date, etc.-slists the size of files, in blocks. Add -h to show the size in a humanly-readable form.
To navigate to a specific folder, use the cd command and a name or path of a directory.
Remember that the names are case sensitive. Use cd without a name or path to return to the user’s home directory.
Useful cd options include:
cd .go to the directory one level higher than your current location.cd -switch to the previous directory.cd /go to the root directory.
Use the cp command to copy a file or directory. You’ll need to include the name of the file and the target location.
To copy file1 from Desktop to Dir1, type in:
To change the name of file1 while copying it to another destination, use this format:
This command copies file1 to Dir1 with a name you specify.
To copy a directory and its contents, use the -r flag in this format:
The mv command works in the same manner as the copy command.
For instance, to move a file to another location, type in:
The touch command allows you to create a new file with any extension.
In the terminal, enter the following command:
For example, to create a system.log file, type in:
To create a directory, use the mkdir command. Diablo 3 beta key generator download for pc. Enter a new directory name or full path in this format:
Or:
To delete a Linux file , use rm in this format:
Ssh Generate Public Key Linux Download
In addition, you can enter a full path:
To delete a directory, add the -r flag to the rm command.
Generate Public Key Ssh Linux
To view the status of all network adapters, use the ifconfig command. Moreover, when you don’t use any options with ifconfig, the output displays only active interfaces.
To clear the current working area of your bash screen, type clear in the shell. This command clears one portion of the screen and shifts up the previous output.
Daemon tools serial key generator. To remove the output from the terminal completely, use the reset command.
Run a Command on a Remote Server from a Local Computer
This method does not create a new shell. Instead, it runs a command and returns the user to the local prompt. You can create a file, copy files, or run any other SSH command in this format.
To remotely execute a command from the local machine, append an instruction to the SSH command. For example, to delete a file, type in:
Enter the password, and the file on the remote server will be deleted without creating a new shell.
The SSH tool comes with many optional parameters. The table below lists common SSH options and the corresponding descriptions.
| SSH Option | Description |
| -1 | Instructs ssh to use protocol version 1 |
| -2 | Instructs ssh to use protocol version 2. |
| -4 | Permits only IPv4 addresses. |
| -6 | Permits only IPv6 addresses. |
| -A | Enables authentication agent connection forwarding. Use this option with caution. |
| -a | Disables authentication agent connection forwarding. |
| -b bind_address | Use this option on the local host with more than one address to set the source address of the connection. |
| -C | Enables data compression for all files. Only to be used with slow connections. |
| -c cipher_spec | Use to select a cipher specification. List the values separated by a comma. |
| -E log_fileName | Attaches debug logs to log_file instead of standard error. |
| -f | Sends ssh to background, even before entering a password or passphrase. |
| -g | Permits remote hosts to connect to ports forwarded on a local machine. |
| -q | Runs ssh in quiet mode. It suppresses most error or warning messages. |
| -V | Displays the version of ssh tool and exits. |
| -v | Prints debugging messages for ssh connection. The verbose mode is useful when troubleshooting configuration issues. |
| -X | Use this option to enable X11 forwarding. |
| -x | Disable X11 forwarding. |
This article has covered the 19 most popular commands for using the SSH tool effectively. Now you can manage your server remotely with an added layer of security and have these commands at your fingertips.
Before executing these commands and options on a live server, we do recommend using a test machine first.
Next you should also read
The article covers the 5 most common and efficient ways to secure an SSH connection. The listed solutions go…
This article provides all the information you need in order to set up SSH encryption on your remote device.…
With this gem you can generate a new secret key base for rails, directly written to config/secrets.yml by capistrano. Installation Add this line to your application's Gemfile. Rails secret_key_base generate. In development mode, a Rails application would use its name as the secretkeybase, and can be easily extracted by visiting an invalid resource for a path. As a result, this allows a remote user to create and deliver a signed serialized payload, load it by the application, and gain remote code execution. Nowadays (rails 6) rails generate a secret key base in tmp/developmentsecret.txt for you. And in production environment the best is having SECRETKEYBASE as en env variable, it will get picked up by rails. You can check with Rails.application.secretkeybase.
Ssh Generate Public Key Linux Windows 10
If you are using Debian 9 or Debian 10 to manage servers, you must ensure that the transfer of data is as…
Ssh Generate Public Key Linux Server
When establishing a remote connection between a client and a server, a primary concern is ensuring a secure…
Linux Generate Public Private Ssh Key
MySQL is an open-source relational database server tool for Linux operating systems. It is widely used in…